How to use Attack Surface Page?
How To Use Attack Surface Page?
NVADR is a platform for managing attack surfaces that is designed to detect all attack surfaces associated with your organization in order to protect them from external attacks. By utilizing NVADR, you can effectively identify security vulnerabilities and gain a better understanding of areas that pose a risk. Through continuous analysis, NVADR is able to detect changes in attack surfaces, which ultimately helps to reduce the risk of cyberattacks.
The attack surface module is further divided into:
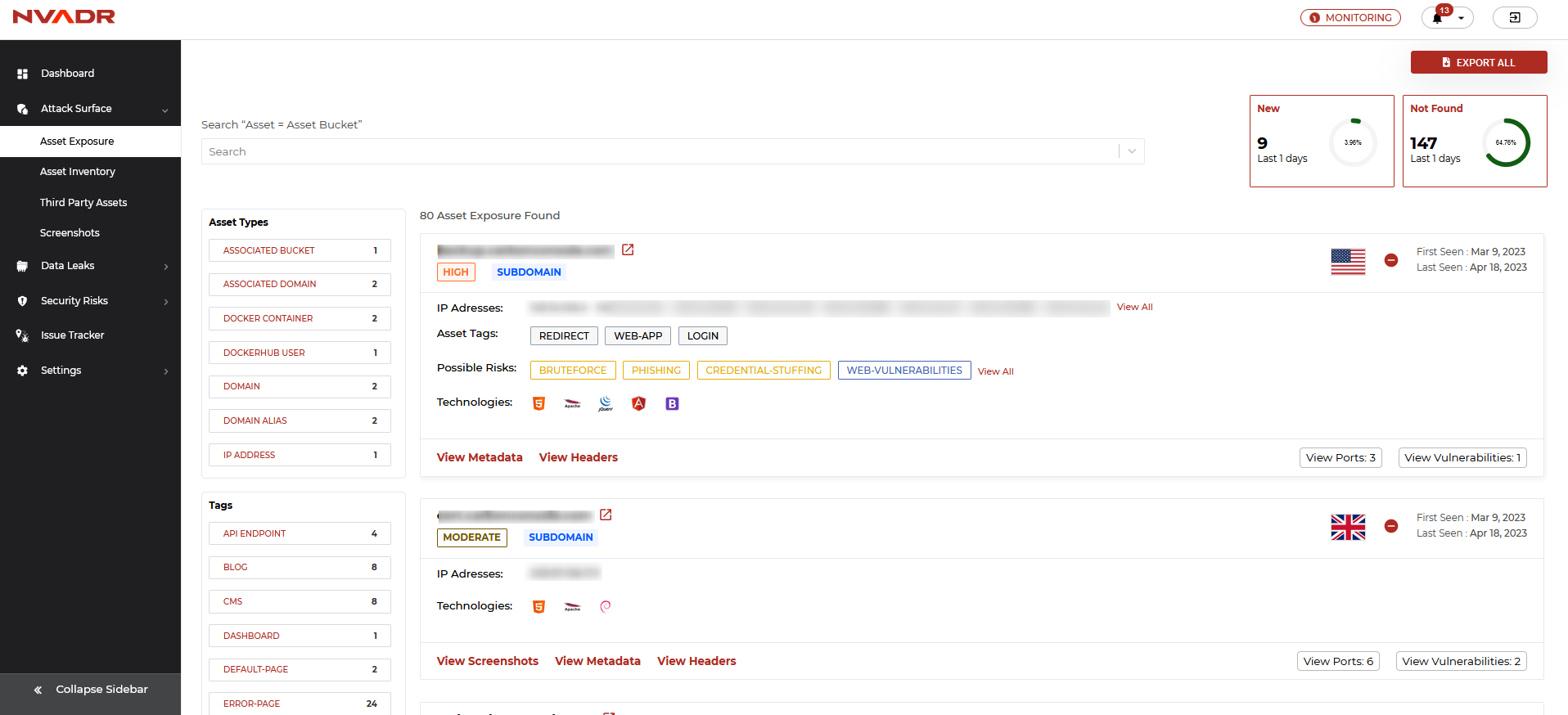
Asset Exposure
- In the 'Asset Exposure' section, you can access a list format containing all the identified assets. Each asset is presented with a corresponding URL, asset type, asset tag, potential risks, cloud classification, first-seen and last-seen dates.
- As the number of discovered assets can be quite extensive, manually scrolling through the entire list can be a time-consuming task. To simplify this process, users have the option of filtering the assets based on their type, tags, and status.
- The assets can be filtered based on asset types and tags. Click on the asset type/tag for which you wish to view the data.
- Another way to filter the assets is based on the asset status, these are the following filters:
- All Active Assets Since: The total number of active assets that have been discovered since the last scan.
- New Assets Since: New assets found in the scans.
- Assets Not Found Since: The total number of inactive assets that have been found.
- You can also use different filters to find Active, new or inactive assets which have been found in the last 7 days, 1 month, 6 months, 1 year or you can also use custom dates to check it.
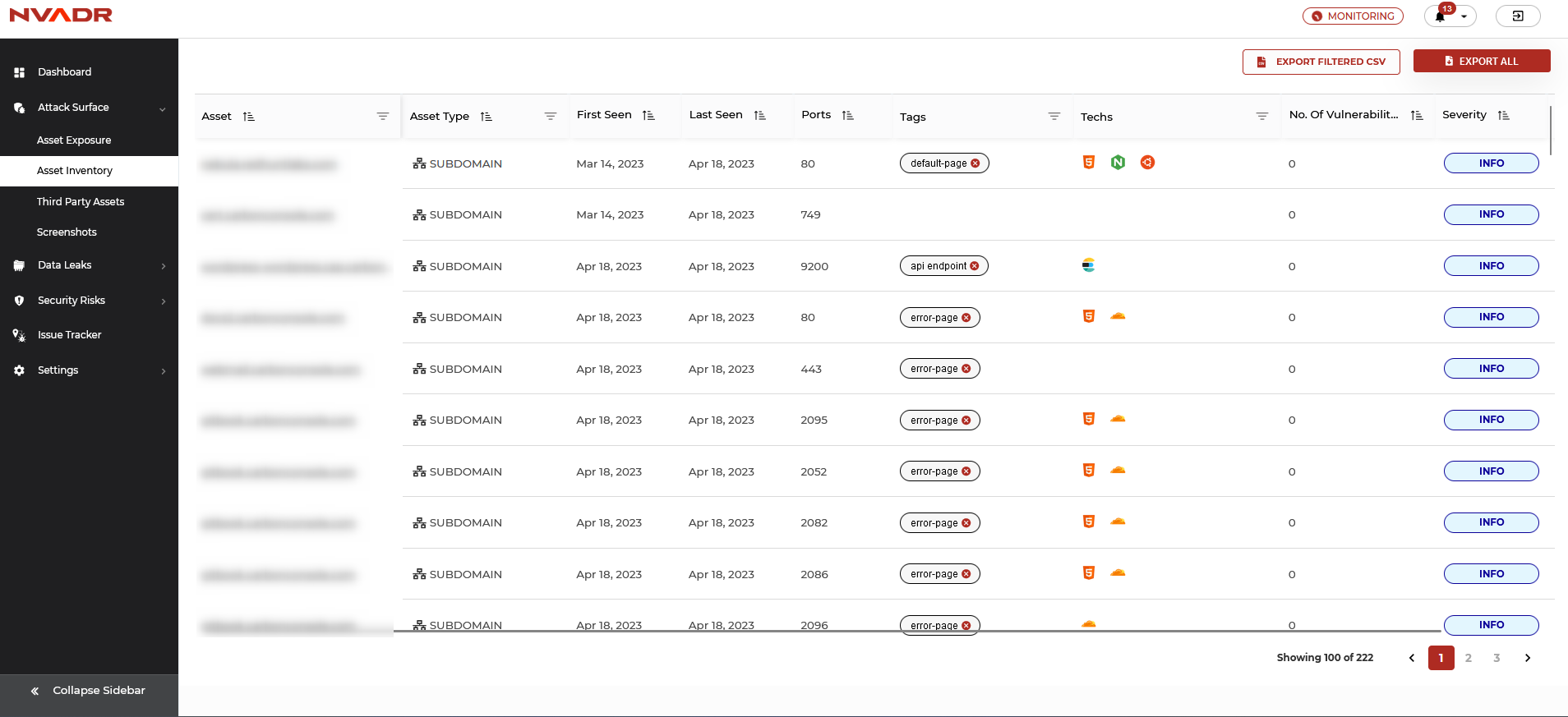
Asset Inventory
- In the 'Asset Inventory' section, all the identified assets are presented in a column and row format.
- Each asset is accompanied by its corresponding asset type, ports, tags, technology utilized in its development, number of vulnerabilities, severity level, and first-seen and last-seen dates.
- Users have the option of filtering the displayed data based on the asset name (URL), asset type, ports, tags, and technology.
Actions:
- To filter data based on asset, ports, or technology, input the asset name, port number, or technology into the designated field.
- To filter data based on asset types or tags, choose the relevant option from the drop-down menu.
- Additionally, within the 'Asset Inventory' section, users have the ability to add tags to selected assets by navigating to the 'Actions' tab, entering the desired tag name, and clicking 'Add'. This feature enables users to create their own customized tags.
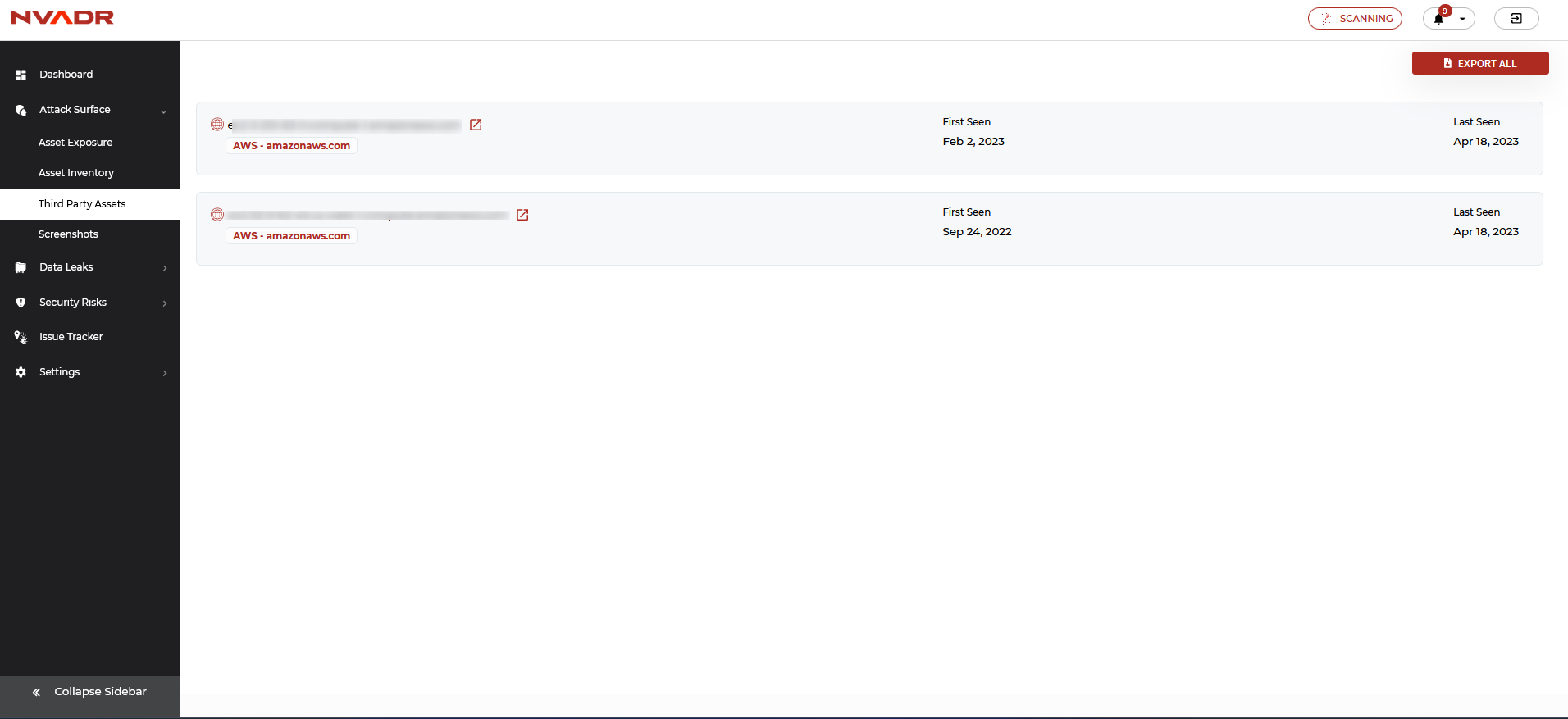
Third-Party Assets
Third-party assets refer to the services or tools utilized by an organization that have been sourced from another organization, either with or without a contractual agreement. Another way to describe third-party assets is as assets that are owned by a vendor outside of the organization.
Cloud-based software services, cloud web hosting services, project management tools. CRM tools, communication tools, etc are a few examples of third-party assets.
- All the discovered third-party assets are displayed under this module.
- The third-party assets screen includes the following information:
- Asset URL and platform used.
- First Seen - Date
- Last Seen - Date
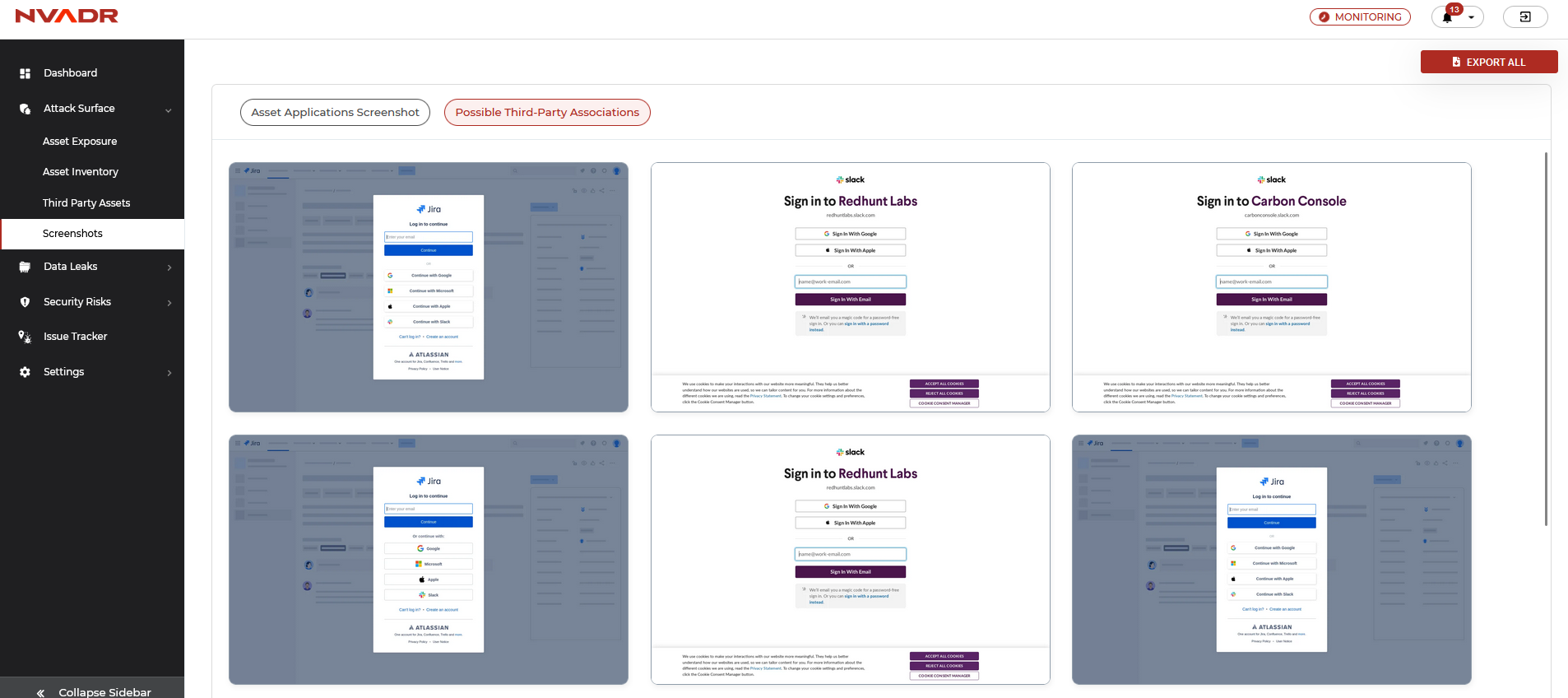
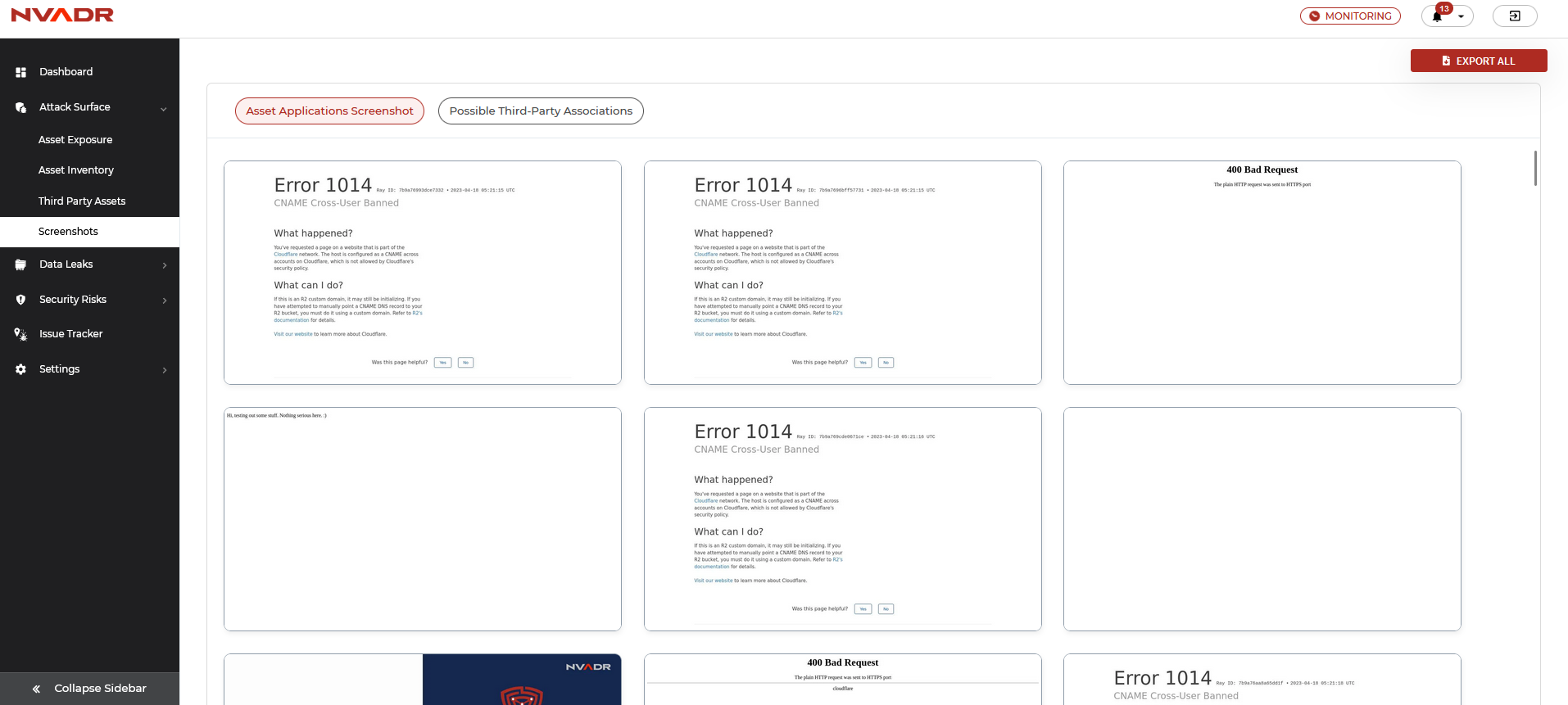
Screenshots
Screenshots refer to visual representations of any unexpected responses or content identified across various ports of the assets that have been discovered. The screenshot module encompasses two distinct tabs: "Asset Application Screenshots" and "Possible Third-Party Associations."
Asset application screenshots displays the screen responses of the assets belonging to the organization.
Possible third-party associations displays the screen images of the discovered third-party assets.